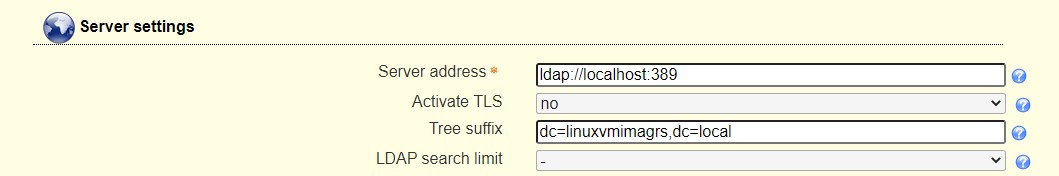
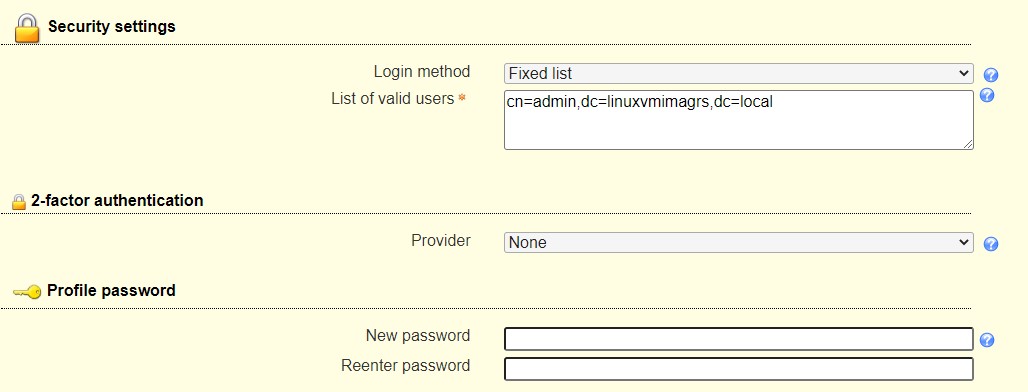
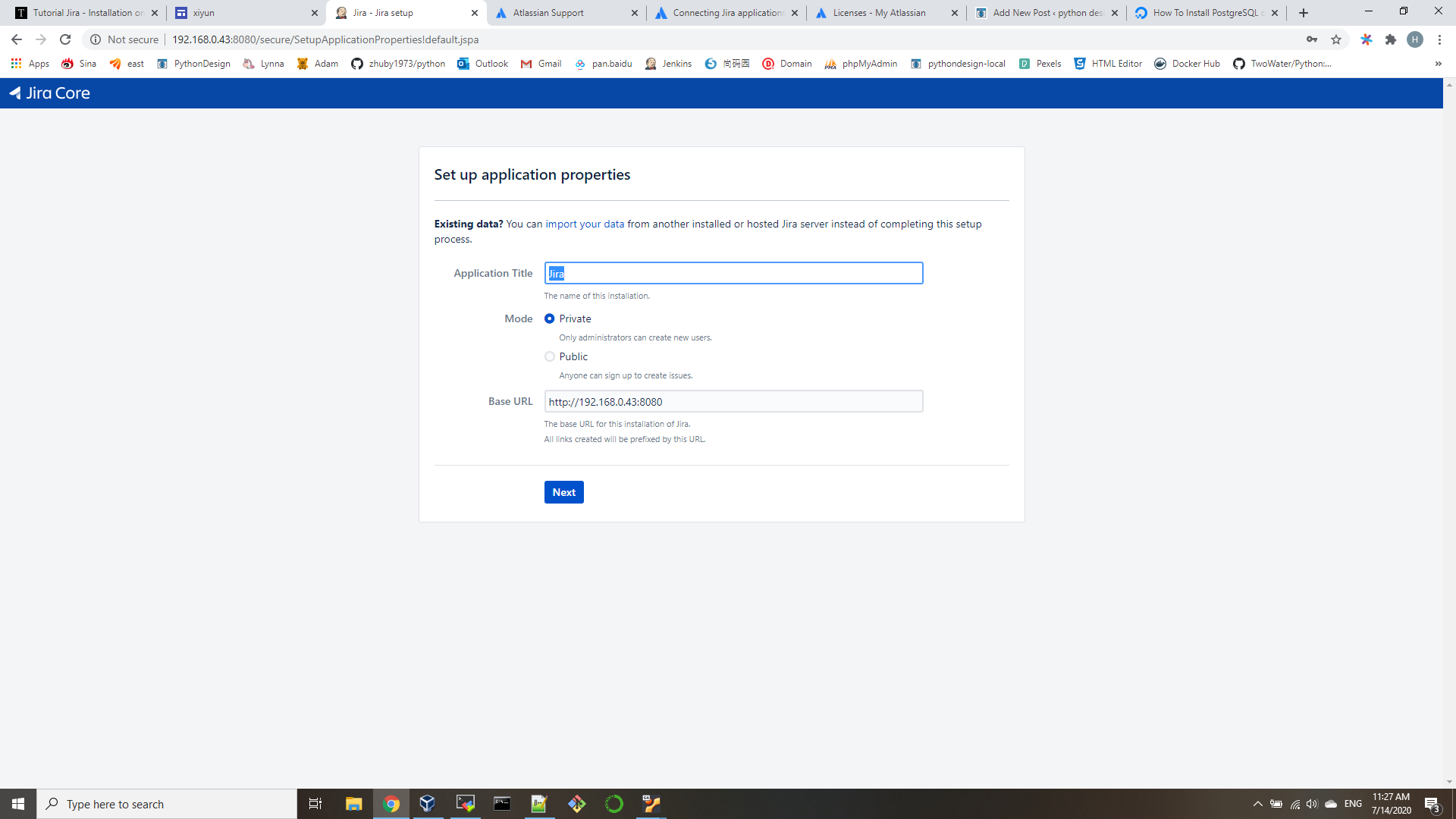
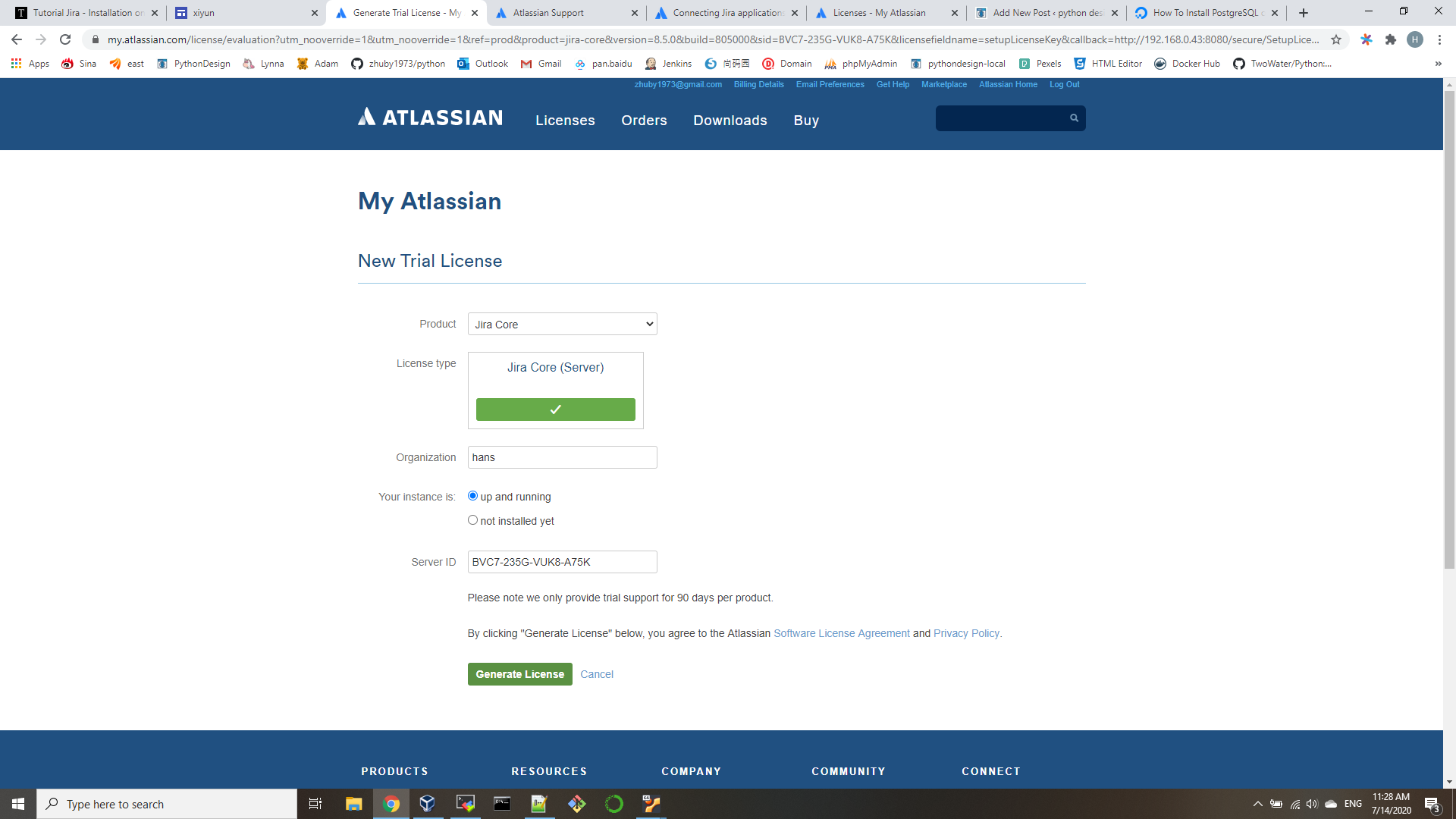
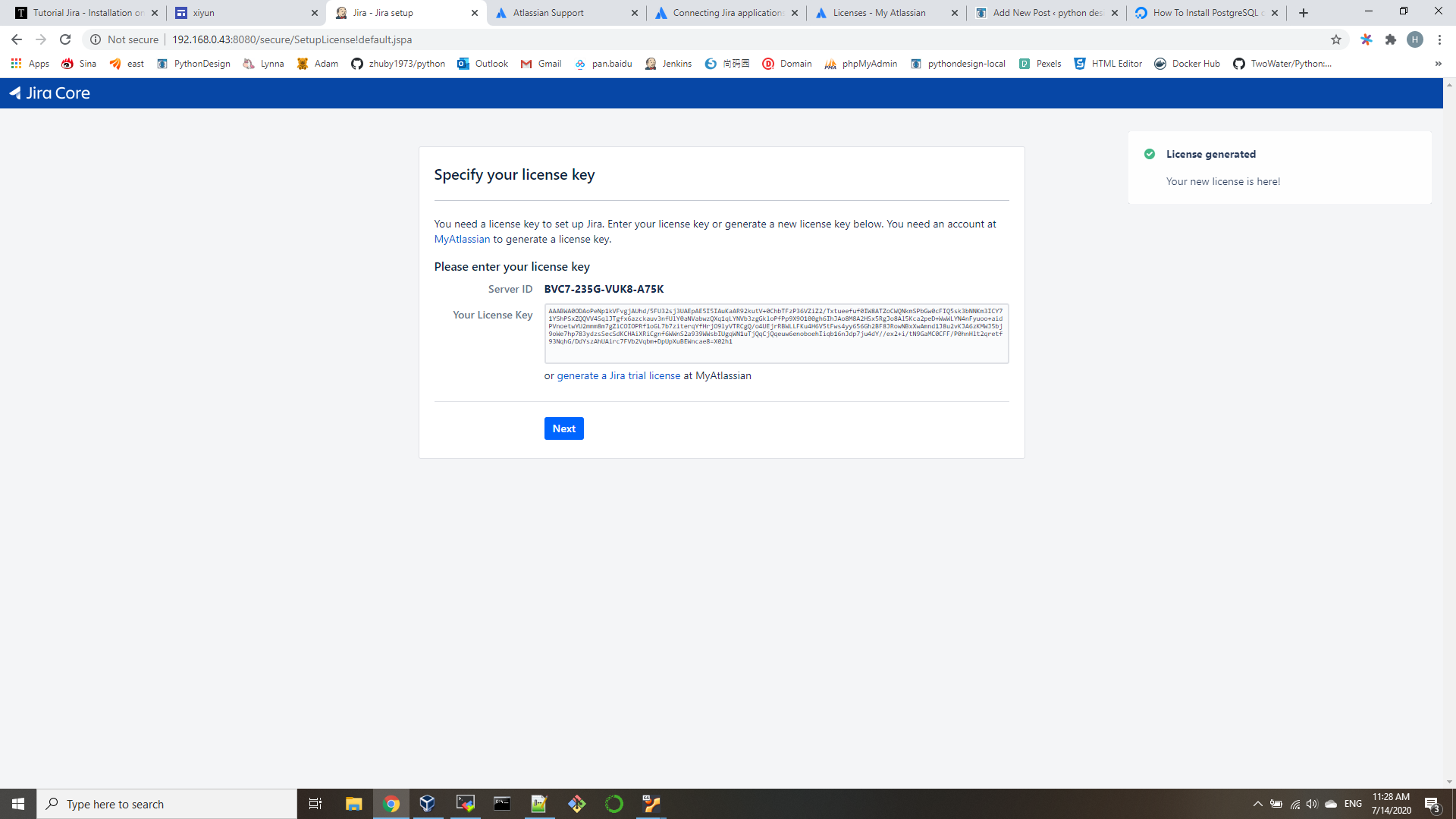
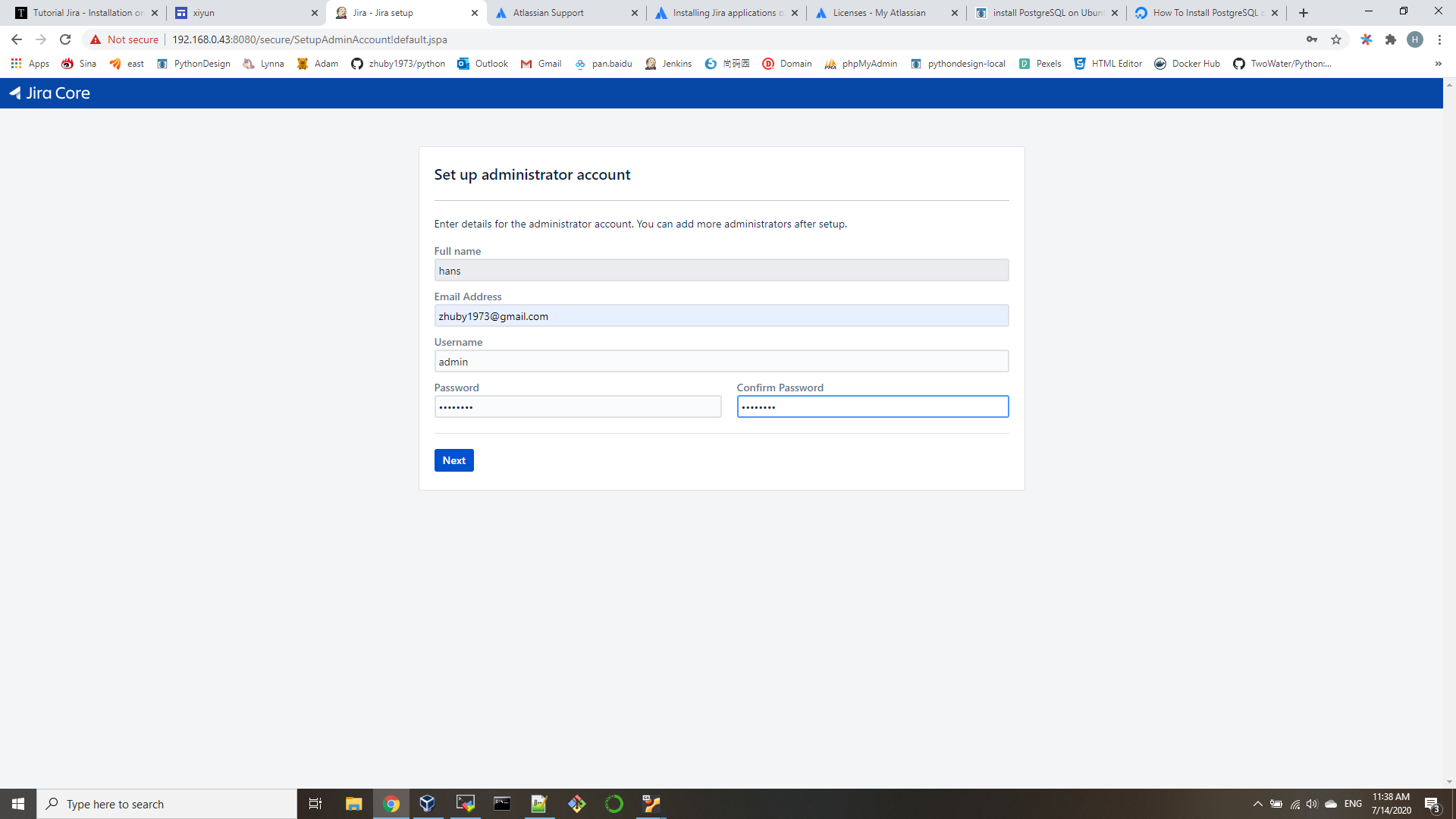
- edit /etc/ansible/ansible.cfg
host_key_checking = False - edit /etc/ansible/hosts
[all:vars]
ansible_connection=ssh
ansible_ssh_user=your_sshid
ansible_ssh_pass=your_sshpassword
ansible_sudo_pass=your_sudopassword
[appservers]
192.168.0.[1-3] - edit playbook.yml
---
-hosts: all
vars_files:
- vars.yml
tasks:
-name: download file from link
get_url:
url:http://github.com/test.txt
dest: /tmp/test.txt
mode: 0755
-name: ensure directory exists
file:
path: "{{ jboss_conf_location }}"
state: directory
owner: jboss
group: jboss
-name: copy file
command: >
cp /tmp/test.txt {{ jboss_conf_location }}
become: yes
become_user: jboss
-name: remove file
file:
path: "{{ jboss_conf_location }}/test.txt"
state: absent
become: yes
become_user: jboss
then you can run it with ansible-playbook playbook.yml
there is another way to store password, ansible-vault create passwd.yml
ansible_ssh_user: your_sshid ansible_ssh_pass: your_sshpassword ansible_sudo_pass: your_sudopassword
then you can run it with command:
ansible-playbook --ask-vault-pass --extra-vars '@passwd.yml' playbook.yml
you can run Shell command with sudo password input:
ansible appservers -m shell -a "source /home/pm2/.bashrc && pm2 status" -b --become-user=pm2 -K
scp files:
- name: Copy configuration files.
copy:
src: "{{ item.src }}"
dest: "{{ item.dest }}"
owner: root
group: root
mode: 0644
with_items:
- src: httpd.conf
dest: /etc/httpd/conf/httpd.conf
- src: httpd-vhosts.conf
dest: /etc/httpd/conf/httpd-vhosts.conf
Make sure Apache or other service is started now and at boot:
- name: Make sure Apache is started now and at boot service: name=httpd state=started enabled=yes
yum install apache or other packages:
- name: Install Apache.
yum:
name:
- httpd
- httpd-devel
state: present
lineinfile edit:
- name: Adjust OpCache memory setting.
lineinfile:
dest: "/etc/php/7.1/apache2/conf.d/10-opcache.ini"
regexp: "^opcache.memory_consumption"
line: "opcache.memory_consumption = 96"
state: present
notify: restart apache
git clone:
- name: Check out drush 8.x branch.
git:
repo: https://github.com/drush-ops/drush.git
version: 8.x
dest: /opt/drush
run command in one line:
- name: Install Drush dependencies with Composer.
command: >
/usr/local/bin/composer install
chdir=/opt/drush
creates=/opt/drush/vendor/autoload.php
create file link:
- name: Create drush bin symlink.
file:
src: /opt/drush/drush
dest: /usr/local/bin/drush
state: link
list files in directory:
- shell: 'ls -ltr /opt/jboss/log/'
register: ps
- debug: var=ps.stdout_lines